The world of cryptocurrency, while offering exciting opportunities for investment and financial innovation, is unfortunately not immune to significant security risks. This article explores the five biggest security threats facing cryptocurrency users today, examining vulnerabilities ranging from exchange hacks and phishing scams to the ever-present danger of malware and private key compromise. Understanding these threats is crucial for all participants in the crypto ecosystem, regardless of experience level, to ensure the safety and security of their digital assets. We delve into each threat, providing insights into how they operate and offering practical strategies to mitigate your risk.
Phishing Scams Targeting Investors

Phishing remains a major threat in the cryptocurrency space, specifically targeting investors. Attackers employ sophisticated techniques to mimic legitimate platforms or individuals, often leveraging the allure of high returns or urgent situations to trick victims into revealing their private keys, seed phrases, or other sensitive information.
These scams often involve convincing emails, fake websites, or even malicious mobile applications designed to steal credentials. The resulting loss can range from minor inconveniences to the complete depletion of an investor’s cryptocurrency holdings. Vigilance and careful verification of all communication and platforms are crucial to mitigating this risk.
Education is key in preventing successful phishing attacks. Investors should be aware of common tactics such as urgent requests for action, unrealistic promises, and suspicious email addresses or website URLs. Regularly reviewing security protocols and employing strong password management practices also significantly reduces vulnerabilities.
Ransomware Attacks in the Crypto Space
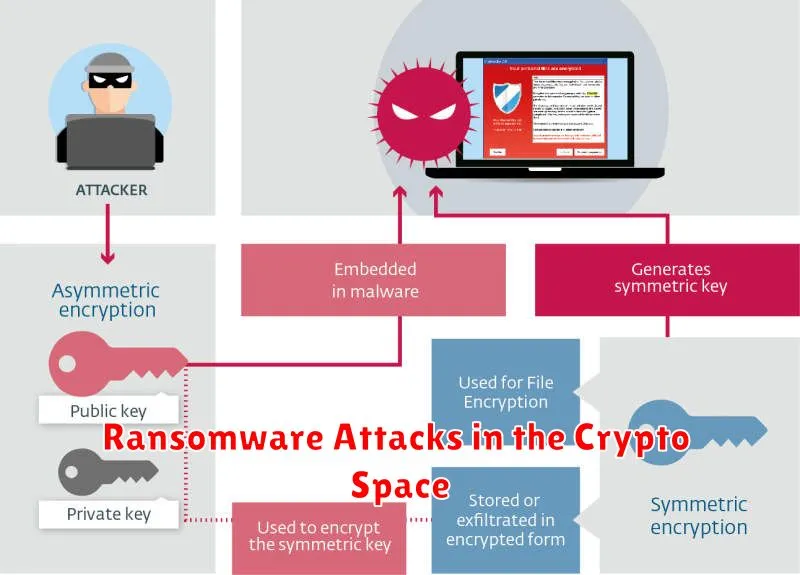
The cryptocurrency space, while offering decentralized and innovative financial tools, remains vulnerable to ransomware attacks. These attacks exploit vulnerabilities in individual wallets, exchanges, or even the underlying infrastructure to encrypt data and demand payment in cryptocurrency, often Bitcoin or other less traceable coins.
Key vulnerabilities include weak passwords, phishing scams targeting private keys, and software exploits within cryptocurrency wallets or exchanges. The anonymity of cryptocurrencies makes them attractive to attackers, as tracing payments and apprehending culprits is significantly more challenging than with traditional financial systems.
The impact of a successful ransomware attack can be devastating. Victims may lose access to significant funds, sensitive personal information, or critical business data. The reputational damage can also be substantial, eroding trust and impacting the value of the affected entity.
Prevention strategies involve implementing strong security practices such as multi-factor authentication (MFA), using reputable wallets and exchanges, regularly updating software, educating users about phishing scams, and maintaining robust backups.
Mitigation efforts may include collaborating with cybersecurity experts, reporting the incident to law enforcement (where applicable), and possibly negotiating with the attackers (although this is generally discouraged due to its potentially enabling future attacks). However, the focus should always be on prevention through proactive security measures.
Hacks on Crypto Exchanges

Cryptocurrency exchange hacks represent a significant threat to the industry. These breaches often involve sophisticated attacks targeting vulnerabilities in the exchange’s security systems, resulting in the theft of large amounts of cryptocurrency from both the exchange itself and its users.
Hackers employ various methods, including phishing scams targeting user credentials, exploiting software vulnerabilities to gain unauthorized access, and utilizing insider threats from compromised employees. The consequences can be devastating, leading to substantial financial losses for the exchange and eroded user trust.
The impact extends beyond immediate financial losses. A successful hack can cause significant damage to an exchange’s reputation, potentially leading to regulatory scrutiny and legal action. Furthermore, it can create a negative perception of the entire cryptocurrency market, hindering its growth and adoption.
Strengthening security measures is crucial. This involves implementing robust multi-factor authentication (MFA), regular security audits, and employing advanced technologies such as blockchain security solutions and cold storage for cryptocurrency assets.
Ultimately, mitigating the risk of exchange hacks requires a multi-faceted approach encompassing technical improvements, enhanced employee training, and a commitment to transparency and accountability from cryptocurrency exchanges.
Social Engineering Attacks
Social engineering attacks represent a significant threat in the cryptocurrency landscape. These attacks exploit human psychology, leveraging trust and manipulation to gain access to private keys, seed phrases, or sensitive information leading to cryptocurrency theft.
Phishing scams, a common social engineering tactic, involve deceptive emails, messages, or websites mimicking legitimate entities to trick users into revealing their credentials. Fake giveaways and investment opportunities also lure unsuspecting victims into sharing their information or transferring funds.
Sim swapping, where attackers gain control of a victim’s phone number to access two-factor authentication (2FA) codes, is another prevalent social engineering attack vector. This allows attackers to bypass security measures and gain unauthorized access to cryptocurrency accounts.
Protecting against social engineering requires a multi-faceted approach. Strong password hygiene, skepticism towards unsolicited communication, and thorough verification of websites and individuals are crucial. Furthermore, users should be wary of unverified apps and software and maintain awareness of the latest social engineering tactics.
Fraudulent Initial Coin Offerings (ICOs)

One of the most significant security threats in the cryptocurrency space is the prevalence of fraudulent Initial Coin Offerings (ICOs). These scams often involve misleading whitepapers, exaggerated promises of returns, and ultimately, the disappearance of investor funds with little to no product or service delivered.
Scammers exploit the hype surrounding new cryptocurrencies, preying on investors seeking quick profits. They create sophisticated websites and marketing materials to appear legitimate, attracting unsuspecting individuals to invest substantial sums.
Lack of regulation in the early days of ICOs contributed significantly to their proliferation. The absence of robust oversight allowed many fraudulent projects to flourish, resulting in significant financial losses for investors.
Due diligence is crucial in mitigating the risk of investing in fraudulent ICOs. Thoroughly researching the project team, examining the whitepaper for inconsistencies, and understanding the technology behind the offering are all essential steps before committing funds.
The consequences of investing in a fraudulent ICO can range from complete loss of investment to legal repercussions, highlighting the importance of caution and thorough research in this volatile market.
